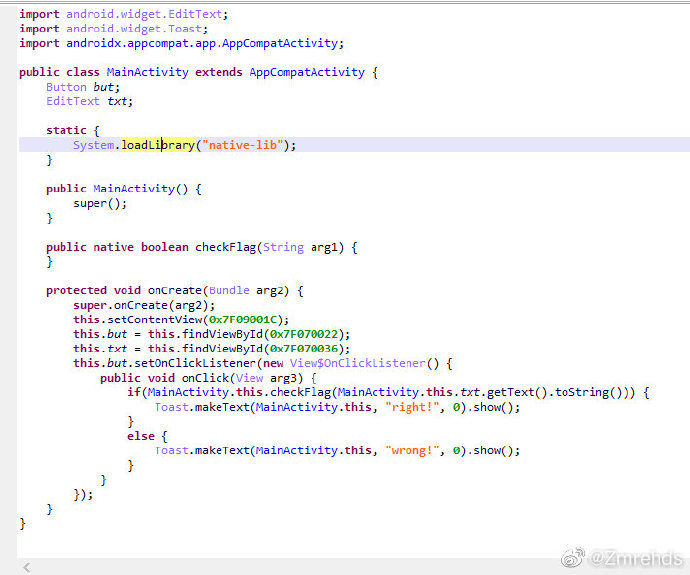
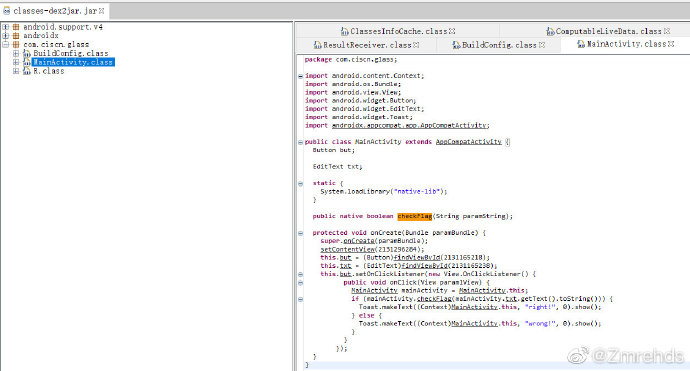
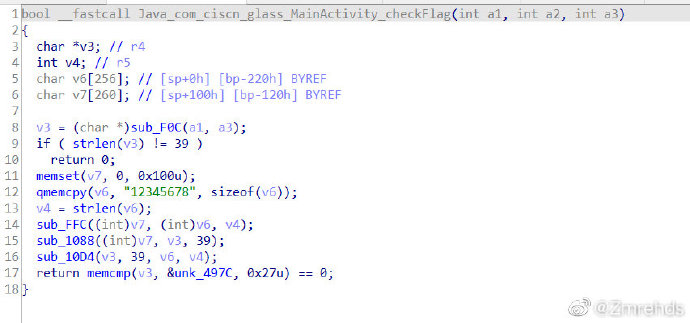
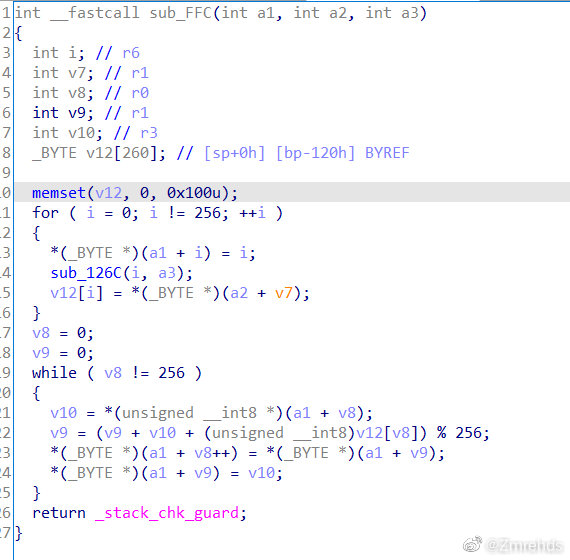
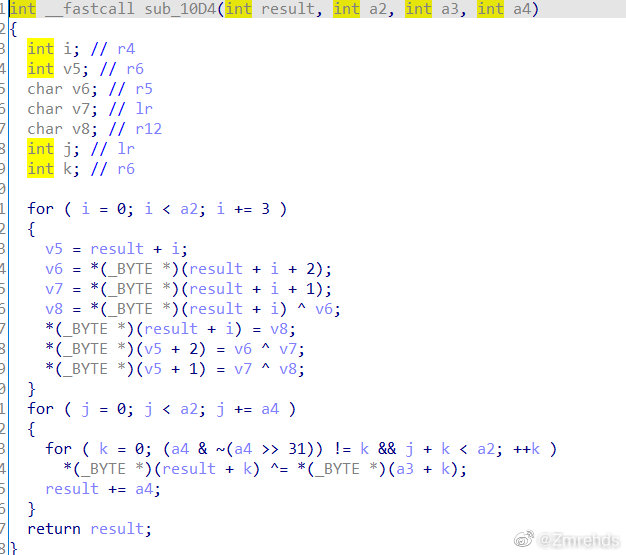
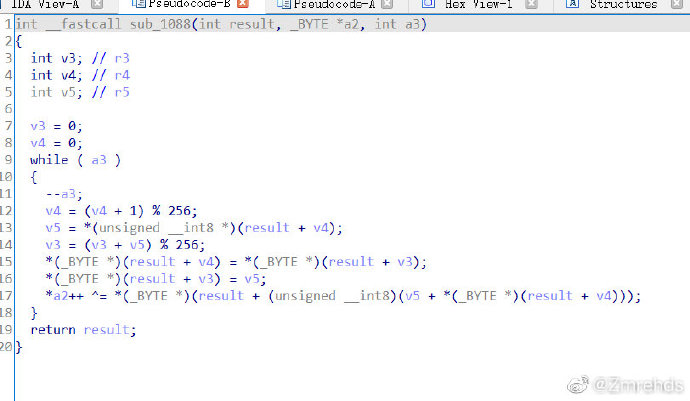
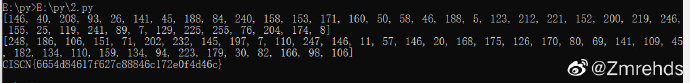
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
| key = '12345678'
key2 = [163, 26, 227, 105, 47, 187, 26, 132, 101, 194,
173, 173, 158, 150, 5, 2, 31, 142, 54, 79,
225, 235, 175, 240, 234, 196, 168, 45, 66, 199,
110, 63, 176, 211, 204, 120, 249, 152, 63]
key3 = [146, 40, 208, 93, 26, 141, 45, 188, 84, 240, 158, 153, 171, 160, 50, 58, 46, 188, 5,
123, 212, 221, 152, 200, 219, 246, 155, 25, 119, 241, 89, 7, 129, 225, 255, 76, 204, 174, 8]
for m in range(0, 5):
for i in range(len(key2)):
j = i % 8
fla = key2[i] ^ ord(key[j])
key2[i] = fla
print(key2)
for i in range(0, 39, 3):
key3[i + 1] ^= key3[i]
key3[i + 2] ^= key3[i + 1]
key3[i] ^= key3[i + 2]
print(key3)
c = key3
t = []
key = '12345678'
ch = ''
j = 0
s = list(range(256))
for i in range(256):
j = (j + s[i] + ord(key[i % len(key)])) % 256
s[i], s[j] = s[j], s[i]
i = 0
j = 0
for r in c:
i = (i + 1) % 256
j = (j + s[i]) % 256
s[i], s[j] = s[j], s[i]
x = (s[i] + (s[j] % 256)) % 256
ch += chr(r ^ s[x])
print(ch)
|